On the one hand adding dependencies to a project is easy, on the other hand securing a project and checking for vulnerable dependencies is way harder.
The OWASP dependency check plugin for Maven allows us to scan our project’s dependencies for know vulnerabilities.
I will demonstrate its usage in the following short example.

Dependencies
We just need to add one plugin-dependency to our Mavenized project’s pom.xml.
The configuration tells the plugin to let the build fail if a CVSS (Common Vulnerability Score System) value of 4 is reached.
<plugin>
<groupId>org.owasp</groupId>
<artifactId>dependency-check-maven</artifactId>
<version>2.1.1</version>
<configuration>
<cveValidForHours>12</cveValidForHours>
<failBuildOnCVSS>4</failBuildOnCVSS>
</configuration>
<executions>
<execution>
<goals>
<goal>check</goal>
</goals>
</execution>
</executions>
</plugin>Sample Project
This is a sample project with one dependency on board, struts-1.2.9 which we now want to scan for vulnerabilities..
<project xmlns="http://maven.apache.org/POM/4.0.0"
[..]
<dependencies>
<!-- sample dependency to scan for vulnerabilities -->
<dependency>
<groupId>struts</groupId>
<artifactId>struts</artifactId>
<version>1.2.9</version>
</dependency>
</dependencies>
[..]
</project>Scanning for Vulnerabilities
Now we’re ready to check our project for vulnerabilities by running mvn dependency-chck:check – please be patient – downloading the vulnerabilities archive takes a while ….
$ mvn dependency-check:check 1 ↵
[INFO] Checking for updates
[INFO] NVD CVE requires several updates; this could take a couple of minutes.
[INFO] Download Started for NVD CVE - 2003
[INFO] Download Started for NVD CVE - 2007
[INFO] Download Started for NVD CVE - 2008
[INFO] Download Complete for NVD CVE - 2003 (1912 ms)
[..]
[INFO] Download Complete for NVD CVE - 2017 (7089 ms)
[INFO] Processing Started for NVD CVE - 2017
[INFO] Download Complete for NVD CVE - Modified (8258 ms)
[INFO] Processing Started for NVD CVE - Modified
[INFO] Check for updates complete (56924 ms)
[INFO] Analysis Starting
[INFO] Creating the CPE Index
[INFO] CPE Index Created (1957 ms)
[INFO] Creating the CPE Index
[INFO] CPE Index Created (0 ms)
[INFO] Analysis Complete (4567 ms)
[WARNING]
One or more dependencies were identified with known vulnerabilities in owasp-dependency-check-sample:
commons-beanutils-1.7.0.jar (commons-beanutils:commons-beanutils:1.7.0, cpe:/a:apache:commons_beanutils:1.7.0) : CVE-2014-0114
commons-collections-2.1.jar (commons-collections:commons-collections:2.1, cpe:/a:apache:commons_collections:2.1) : CVE-2015-6420
commons-fileupload-1.0.jar (commons-fileupload:commons-fileupload:1.0, cpe:/a:apache:commons_fileupload:1.0, tomcat:commons-fileupload:1.0-5.5.23) : CVE-2016-3092, CVE-2016-1000031, CVE-2014-0050, CVE-2013-0248
struts-1.2.9.jar (cpe:/a:apache:struts:1.2.9, struts:struts:1.2.9) : CVE-2016-1182, CVE-2016-1181, CVE-2015-0899, CVE-2014-0114
See the dependency-check report for more details.
[INFO] ------------------------------------------------------------------------
[INFO] BUILD FAILURE
[INFO] ------------------------------------------------------------------------
[ERROR] Dependency-Check Failure:
[ERROR] One or more dependencies were identified with vulnerabilities that have a CVSS score greater then '4.0':
[ERROR] commons-beanutils-1.7.0.jar: CVE-2014-0114
[ERROR] commons-collections-2.1.jar: CVE-2015-6420
[ERROR] commons-fileupload-1.0.jar: CVE-2016-3092, CVE-2016-1000031, CVE-2014-0050
[ERROR] struts-1.2.9.jar: CVE-2016-1182, CVE-2016-1181, CVE-2015-0899, CVE-2014-0114Reports
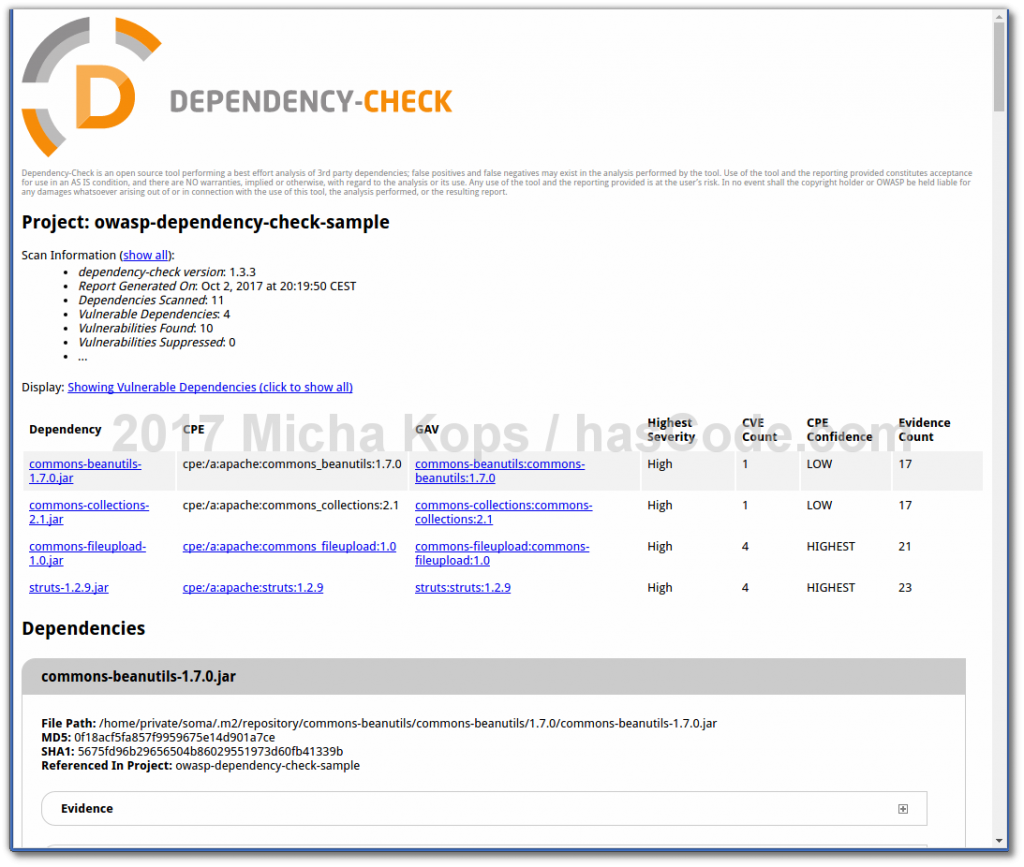
Running the vulnerability check above produces a report named dependency-check-report.html in our target directory that should look like this one:

Suppressing False Positives and False Negatives
We may suppress failures for specific dependencies or artifacts.
The most easiest way is to use the snippet generator from the report view to copy suppressions like this:

We’re storing this snippet in the following file named suppressions.xml:
<?xml version="1.0" encoding="UTF-8"?>
<suppressions xmlns="https://jeremylong.github.io/DependencyCheck/dependency-suppression.1.1.xsd">
<suppress>
<notes><![CDATA[
file name: commons-beanutils-1.7.0.jar
]]></notes>
<gav regex="true">^commons-beanutils:commons-beanutils:.*$</gav>
<cpe>cpe:/a:apache:commons_beanutils</cpe>
</suppress>
</suppressions>Then we just need to reference this file in the plugin configuration in our pom.xml like this:
<plugin>
<groupId>org.owasp</groupId>
<artifactId>dependency-check-maven</artifactId>
<version>2.1.1</version>
<configuration>
[..]
<suppressionFiles>
<suppressionFile>suppressions.xml</suppressionFile>
</suppressionFiles>
</configuration>
[..]
</plugin>When running the checks now, the suppression is applied and shown in the final report:

More detailed information about suppression configuration can be found in the project’s documentation here.
Tutorial Sources
Please feel free to download the tutorial sources from my GitHub repository, fork it there or clone it using Git:
git clone https://github.com/hascode/owasp-dependency-check-tutorial.git